how does carding work|What Is Carding? The Fraud Technique Ruining Your : Tagatay How does carding work? The criminals — also known as carders — use different methods to get credit card numbers. This includes phishing attacks and buying .
Online trackers are everywhere, and they track things like your habits and behavior on certain sites. Laura Michelle Davis/CNET. DuckDuckGo identifies and blocks these online trackers from sites .
PH0 · What Is Carding? The Fraud Technique Ruining Your
PH1 · What Is Carding? How It Works, Prevention Methods, and Examples
PH2 · What Is Carding and How Can You Stay Safe From It?
PH3 · What Is Carding and How Can You Stay Safe From
PH4 · What Is Carding
PH5 · Understanding Carding: A Guide for Awareness & Education
PH6 · Carding: What it is and how to prevent it
PH7 · Carding: What it is and How to Prevent it
PH8 · Carding: What is it and how can you avoid it?
PH9 · Carding: What Is Carding Attack and How Does It Work?
PH10 · Carding: What Is Carding Attack and How Does It
PH11 · Carding
Find binge-worthy recommendations for cable and streaming on ClickTheCity. Get the latest on must-watch TV shows, exclusive trailers, and star interviews. Find binge-worthy recommendations for cable and streaming on ClickTheCity. ClickTheCity. Movies TV Food & Drink Shops & Services. Tickets Menu.
how does carding work*******Carding typically starts with a hacker gaining access to a store’s or website’s credit cardprocessing system, with the hacker obtaining a list of credit or debit cards that were recently used to make purchases. Hackers might exploit weaknesses in the security software and technology intended to . Tingnan ang higit paCarding is a form of fraudwhere stolen credit or debit card information is used to charge prepaid cards, purchase gift cards, or assist other schemes. Stolen cards can be used to . Tingnan ang higit paCompanies are implementing various techniques to stay ahead of carders. Some of the more interesting recent changes include requiring more information from the user that is not as easily available to the carder. Tingnan ang higit pahow does carding workCarding is a crime that often involves the purchase of gift cards which can then be spent on relatively difficult-to-trace goods. The goods . Tingnan ang higit pa Carding itself is defined as the illegal use of the card (Credit/Debit) by unauthorized people (carder) to buy a product. For educational purposes, I will now . How does carding work? The criminals — also known as carders — use different methods to get credit card numbers. This includes phishing attacks and buying . Carding is a type of cybercrime in which criminals, known as “carders,” acquire stolen credit card numbers and use bots to verify which are valid. This type of . How does carding work? Carding fraud is a relatively simple process. Criminals (also known as “carders”) steal your credit card details. They’ll then verify that .How Does Carding Work? The process of executing a carding attack typically involves several steps: Obtain Credit/Debit Card Information: Carders obtain credit card information by stealing physical credit cards, .
What Is Carding? The Fraud Technique Ruining Your Carding is a general fraudster term for using stolen credit and debit card data for personal gain – which can be selling the data, using them to buy goods, or using them to power further fraud.
How Does Carding Work? Carding typically works in the following steps. Step 1: Card Details Are Stolen. The first step for conducting carding is getting details of the credit card. This can be done . How Does Carding Work? Carding is a type of credit card scam in which a criminal steals or fraudulently uses credit card details to buy prepaid gift cards. After they get your details, criminals test the .Overview. [] These ordered fibres can then be passed on to other processes that are specific to the desired end use of the fibre: Cotton, batting, felt, woollen or worsted yarn, .
Carding or hacking is an unauthorized 3rd-party attack. These hackers steal credit card details to buy prepaid gift cards. Plastic money frauds can be avoided by users by ensuring the website’s . In carding attacks, cybercriminals use bots to make fraudulent purchases with stolen credit cards, debit cards, or gift cards. . How Do Carding Attacks Work? The typical steps in a carding attack are: The carder acquires a list of credit card numbers, often through phishing scams, site compromise, or by purchasing lists of stolen numbers on .How Does Card Cloning Work? Card cloning is a fairly elaborate criminal scheme. More specifically: An accomplice is recruited – someone with physical access to credit cards e.g. a cashier, restaurant server etc. . Carding by hand. Before carding machines existed, the process of carding was an exhausting manual process. One method required the use of hand carders, which are small paddles fitted with small cards (known as flick cards) that are used to flick the ends of a lock of fibre and remove strands for spinning off.How Carding Attacks Work. Although there are multiple types of carding attacks, they generally follow the same pattern: The attacker finds a website or online store that does not have adequate security measures in place to protect against fraud. The attacker uses stolen credit cards or counterfeit credit cards to make purchases on the site.how does carding work What Is Carding? The Fraud Technique Ruining Your How carding works Stealing card information. The process of carding begins with card thieves, known as “carders,” who steal credit card information through means such as phishing, skimming, conducting data breaches, or keylogging.. Phishing: Carders use deceptive emails, websites, or messages to trick individuals into revealing .Carding is a term of the trafficking and unauthorized use of credit cards. [1] The stolen credit cards or credit card numbers are then used to buy prepaid gift cards to cover up the tracks. [2] Activities also encompass exploitation of personal data, [3] and money laundering techniques. [4] Modern carding sites have been described as full-service commercial .
A controlled carding function is key for the quality of any nonwoven. This animation focuses on the carding process. A cylinder and worker roller with typica. Carding typically works in the following steps. Step 1: Card Details Are Stolen The first step for conducting carding is getting details of the credit card. This can be done through one of the aforementioned methods, like phishing, skimming, etc. Step 2: Card Details Are Tested. Once the details of the credit card are obtained, they need to .Carding is a type of fraud where an unauthorized thief steals someone’s credit card number and then ensures it is working. They use them to buy prepaid gift cards, and they can also sell the cards or use them to purchase other goods. How Does Carding Work? Carders use sophisticated techniques to test the validity of stolen credit card data. They often perform small transactions to check if the card is active and has available credit. .
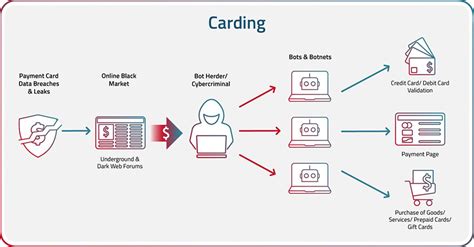
How does carding work? Today, carding usually includes phishing or malware attacks and cybercriminals trading the stolen credit card information on illegal websites. They either hack the store or the . At Shepherd’s Dream we work closely with Woolgatherer Carding Mill, located just down the road from us in Montague, California.Woolgatherer supplies all the wool we use to make our natural . How a Carding Attack Works. A carding attack typically follows these steps: An attacker obtains a list of stolen credit card numbers, either from a criminal marketplace or by compromising a website or payment channel. Their quality is often unknown. The attacker deploys a bot to perform small purchases on multiple payment sites. Carding is a mechanical process that breaks up locks and unorganized clumps of fiber and then aligns the individual fibers so that they are more or less parallel with each other. Carding can also be used to create blends of different fibers or different colors. Carding plays a crucial role in all spinning cycles particularly in the woolen .

The working of a carding machine can be understood in the following steps: CHUTE FEED SYSTEM: The fibre mat to be fed in the carding requires a high degree of evenness (uniformity). This evenness of the fibre mat ensures consistent opening and carding .in the carding process. This evenness is obtained through using the chute .
How does a carding attack work? Like any form of fraud attack using malicious bots, carding can be done quickly and in bulk. To start with, the transaction will seem like normal human behaviour, which it often is. An account may be registered if required, and a few items may be added to a shopping basket. By mimicking genuine .Prior to carding, an accurate amount of synthetic processing lubricant and water is mixed together and applied to the now blended and conditioned scoured loose wool. The purpose of the lubricant is to reduce fibre to metal friction and water reduces the formation of static. . a stripping action, which works in conjunction with the carding .
Learn about Myrna Castillo on Apple TV. Africa, Middle East, and India See All
how does carding work|What Is Carding? The Fraud Technique Ruining Your